Emv Chip Writer Software
I need somebody who have got MCR200 software to re-sell or who can write a software fór my MCR200 to able to read/write chip information for intelligent cards, credit score credit cards. The device model is MCR200 Multifunctional Readers (Magnetic card, Wise card viewer writer) can study/write suitable MSR606 MSR206, I wish to become capable to read and create the info from one chip credit card to another regardless of whatever kind of cards it can be.
Allow me know the cost and everything. Thanks a lot in Progress. Skills:, Observe a lot more:,.
EMV Reader Writer Software v8,Acr 38 Software,MCR 200 Software,ACR 92 Software,Omnikey Software,IC software. Software provided for only magnetic card Reader or Writer.For EMV IC Card (chip card) Reader or Wirter, customization needed. Read or write EMV IC Card. Support PBOC2.0, EMV. Smart Card Reader Writer. The full support and compliance to EMV 2008 and GSA FIPS 201 expand the use to. Software and functionality compatible.
In October 2014, KrebsOnSecurity that searched for to exploit implementation weaknesses at U.T. Financial organizations that were in the procedure of shifting to more protected chip-based credit and debit cards. Nowadays's write-up appears at one provider provided in the cybercrime underground to help robbers perpetrate this type of fraud.
Financial institutions last yr reported receiving tens of thousands of dollars in deceitful credit and debit card transactions arriving from Brazilian and hitting card accounts taken in current retail heists, primarily cards compromised as part of the. The affected banks were confused by the attacks because the deceptive transactions were all posted through Visa and MasterCard‘beds networks as chip-enabled dealings, also though the banking institutions that issued the credit cards in query hadn't yet started sending clients chip-enabled credit cards. Vendor in subterranean forum represents his “Trend” software to perform EMV cards scams against banks that dreamland't applied EMV fully. Fraud experts said the most likely explanation for the exercise was that crooks were pushing regular permanent magnetic stripe dealings through the cards network as chip cards purchases using a method known as a “replay” strike. Relating to one bank interviewed at the period, MasterCard authorities explained that the robbers were likely in control of a transaction port and experienced the ability to manipulate data fields for transactions put through that airport terminal. After taking traffic from a real chip-based chip cards deal, the thieves could put in stolen credit card data into the purchase stream, while changing the vendor and acquirer bank account information on-the-fly. Lately, KrebsOnSecurity came across a fraudster in a well-known cybercrime forum promoting a pretty advanced software-as-a-service bundle to perform simply that.
The seller, a hacker who apparently is experienced in marketing skimming products to help thieves steal card data from ATMs ánd point-of-saIe products, phone calls his product “Revolution” and provides to provide buyers with a list of U.S i9000. Financial institutions that have got not fully or properly implemented systems for accepting and validating chip-card dealings. Very first, a little bit of history on chip-based cards is usually in order. Chip cards are associated with a standard called EMV (brief for ), a worldwide payment program that has already become followed by every some other G20 country as a more secure choice to cards that basically store account holder information on a credit card's magnetic stripe. EMV cards include a safe microchip that will be made to make the credit cards very tough and costly to fake. There are several checks that banking institutions can use to validate the authenticity of chip card transactions. The chip shops encrypted data about the cardholder account, as well as a “cryptogram” that enables banks to tell whether a cards or deal has been recently improved in any way.
The chip furthermore consists of an internal “counter” mechanism that will get incremented with each sequential purchase, so that a copy counter worth or one that skips ahead may suggest data burning or some other scams to the loan company that issued the cards. It appears that the Development software is definitely developed to focus on banks that are in the process of architecting their transaction networks to deal with EMV transactions, but that even so aren't however properly checking out the EMV cryptógram and/or table for these transactions.
It also appears that some banks have got inexplicably reduced their scams controls on EMV transactions, even though they are not yet taking advantage of the included security protections offered by chip-based cards. “The cause I think they trouble to made up EMV dealings is certainly that they understand the EMV cards issuing banks rest their fraud controls on them and don't have it applied correctly and as a result they do not properly check out the powerful EMV information,” mentioned Avivah Litan, a scams expert with. That's exactly what the fraudster selling Evolution factors óut in his somewhat awkwardIy-worded product sales thread for his item, which he mentioned relies on software capable of creating to chip ánd mag-stripe centered cards. Java Card pertains to a software technologies that enables Java-based applications (applets) to become run safely on sensible cards and very similar small memory footprint devices. Java Credit card is definitely the tiniest of Coffee platforms qualified for embedded gadgets, and was originally created for the purpose of protecting sensitive info stored on.
“The great news can be that Us is moving to EMV,” he is currently writing. “ This software works with Java cards work with stationary EMV safety not with powerful. Static means the table remains the same every transaction. The point to add is that I will offer from a great deal of banking institutions that utilizes stationary some of them that provides been examined on it after purchase. Visualize how many banks using STATIC!“ This exact same fraudster seems to be the user of an on-line store called “Final Carding,” which markets stolen credit score cards and contains a amount of tutorials on how to conduct card scams. The crook running this web site states he'h online double a day, but that he takes Sundays off. Interestingly, the clock on his Web store says he functions on Central America time (-06:00 GMT).
Java is a highly secure and safe programming vocabulary just about everywhere.except. inside internet browsers.
It's quite hard to hack.into. programs created in Java. The issue is that Coffee is course of action as well “over-powered” fór a web-browsér atmosphere.
A Coffee program is certainly simply like an.exeit can mess with pretty very much everything on your personal computer. For composing “real programs”, which you install on your computer purposely and suggest to have got full accessibility, it's excellent. But this can make the capability to introduce “applets” - essentially full Coffee programs (with all the rights and benefits thereof) - into a web page just as stupid as starting.exe attachments on strange email messages. This is certainly why Brian always suggests “ditch Coffee if you don't want it, but if you do, at minimum unplug it fróm your browser”. UnpIugging Java from the internet browser removes the safety gap (applets) while keeping the capability to install and run Java applications.outside. the internet browser - that is definitely, for software you'd intentionally enable on your computer by operating an.exe. In this capability, Java is certainly highly secure - that system you simply installed will become significantly harder to hack than if it had been created in an “unsafe” language like G or C.
As an example, the OpenOffice.org office collection (a free of charge rival to Microsoft Office) is usually written mainly in Java. This can make it long lasting to many of the assaults that Office (written in a mixture of D and C) is vulnerable to. OpenOffice needs Coffee to become installed on your computer, but it does not need it to be enabled in your browser - because it'h not making use of the well known “applets” function.
In this lighting, Java will be an superb (certainly, perfect) choice for encoding a chip-enabled credit score credit card. It doesn't assurance that the execution itself will be airtight (the developers still have got to obtain all the crypto perfect, which is definitely a problem in itself), but it will perform a lot to mind off assaults.on the card firmware itself. - for instance, from a malicious terminal seeking to hack the chip and pull sensitive data off it. It is dependent on the situation, if the banking institutions is already issuing EMV cards then their documentation program would have the ablitiy to validate the cryptograms and dynamic information, they simply possess to select to perform so and “turn on”that features. If a bank has not issued EMV credit cards at all, after that approval of the cryptogram may not become an option on their program.
In this situation what company should perform is decrease all transactions with a POS access mode requirements that do not create sense structured on the items they concern. For instance if an company does not really issue credit cards with RFID technologies (Paywave/PayPass) then they should possess a principle that diminishes all POS settings that symbolize RFID.
In this situation had the non EMV issuer acquired a rule to decline everything with a POS mode of 05 (chip) they would have got been fine. It is certainly much much easier for several of us to guarantee that we are usually not robbed of our cash then to protected credit cards. With cash, it can be not too tough to avoid locations where you are usually likely to be robbed. Not only that, but you understand right then and now there if it happens. Credit credit card theft is certainly generally invisible. I don't carry huge quantities of money, but I perform many of my daily spending with it.
Cards are just utilized for the huge issues or on the internet purchases. Also using money makes it very much more difficult to track my buying styles, and I including that mainly because well.
Nicely, I have always been over 50, and I possess never ended up swindled. I simply put on't worry about somebody trying to grab my cash. lt isn't like l have all that much anyways, but it can be good enough to obtain me through the day without getting anything. The issue with someone stealing your credit card can be that it starts the door to additional forms of identification thievery, and then you require to maintain an vision on your claims, you might require credit monitoring, or a total deep freeze. And it can become a true nuisance if your card gets blocked while you are usually on the road somewhere and you can't pay out for a resort room because your cards number obtained stolen at a lunchtime table.
You men are lacking my point. When a credit score cards or credit card details is thieved and utilized fraudulently it can be not really YOUR money that is certainly being thieved. It belongs to the bank. I would rathter place the loan company's cash at danger than my personal. They can pay for to get the risk. Plus it's fictional “money” produced out of thin air, so it will be very simple to substitute. Just produce more.
Also getting your credit card information taken is not really the same thing as identity fraud. The just personal details on a credit card can be your title. All the additional inforation belongs to the bank or investment company. Go through your credit card agreement. >Oddly enough, the time clock on his Web store states he functions on Central North america time (-06:00 GMT).
Recognition that the banking institutions who initially documented this fraud pattern stated the fake chip-card transactions made an appearance to end up being emanating from Brazil. If precise, that would place this criminal in Acre, a condition in the north area of Brazilian. As there a great deal of Brazilians traveling and purchasing in USA, mainly in Miami/Orlando,it is certainly organic that Brazilian cards are typical. But how you finish that is Acre? Acre is certainly UTM-5.
UTM-6 can be Mexico partially. There are a very few merchants in our region that are cash just. One is usually an incredibly popular pub with hundreds of customers AND no one particular under 21 is admitted. One would think this location would suffer tremendously but not therefore!
So people wear't let cash only prevent them from going presently there. I proceed and simply make certain I possess cash. It'beds not mainly because inconvenient as one might think to use money at one or two merchants, but to perform therefore at all retailers would consider some modification for sure but could become completed as it was accomplished before cards ever arrived along.
Emv Chip Writer Software
However, by now plastic is so recognized and anticipated I don't believe a money technique would quit the fake card bad guys but it would at minimal hold you from being a victim of your personal card. Shedding the use of charge cards runs counter top to a main development and isn'testosterone levels generally a good concept for a company with longevity dreams.
Rural areas possess a major publicity to criminal offense and retrieved cash is tough to determine. For all the brains out right now there there provides to become a system that provides for protected dealings in all paths of commerce, reduces danger, does not impose major burdens on the customer, or include huge expenses to merchants, and will be straight ahead for providers. I know there is definitely one. Where are usually the others? Jónathan @nc3.mobi. Definitely he must end up being a small merchant, therefore why even bother with EMV right now?
I take care of credit protection for a medium sized, multi-state merchant, and we simply even aren't pressing EMV. We are ONLY rolling it out as we substitute credit score swipe machines that break up. You dont HAVE to implement EMV by the finish of the year, you simply take the liability for fraud at your store IF EMV would have got prevented that scams. Its just a mathematics task, if your yearly fraud numbers are usually. Malayalam drama script pdf.
Yes, the seller's announcement wording is usually strange, small opinion: I believe by this ‘Stationary indicates the testosterone levels2remains the same every purchase. ‘ he indicates Monitor2 and not really ATC (‘counter' as in Brián's tránscript), i.age. This attack is attempting to wrong use magstripe information put into chip which can be easily discovered and transaction dropped - of training course it depends on encounters, correct execution and money invested initial (Brian please take this positively - enhancement of educational post on this fantastic web).
Being an Western european it amazes me often how unsuspecting US banking institutions are. This type of fooling aróund with EMV data has happen to be identified for ages.
CVV3, producing EMV data from mag stripe information, static versus powerful etc.) Why do US banks do not understand from earlier lessons? I would suggest US clients to maintain on making use of plastic instead of credit cards. That will just raise the overall fraud quantity, which seems to become the only cause for the banks to stage up on the plate. That furthermore provides me to the point of EMV+Personal, another example of short term strategy, rather than a lengthy term outlook.
Plus it places (once again) the burdon on the service provider for confirmation. Wake up US banks, altough the People might be seen as the “greatest country on earth”, the aliens outsidé of the US might possess interesting experience to pay attention to. “plastic material instead of cards.”? Also: The closest items to “very long term outlook” seems to become repair Tuesdays and thé goings-on ón Facebook and Twitter. The reduction of the IT dept. In favor of outsourced fog up based providers that different companies appear to become more interested in is certainly something to discover where these problems are worried. From the corp.
Sai production suite 10 serial keys. Stand up stage: That's what we spend our companions to get treatment of. From the individual user have point: I wear't want to get care of it; Microsoft, Apple company, and government rules will take care of everything for me. PIN is not really that helpful at preventing fraud. It may decrease your lost/stolen fraud but that accounts for much less than 10% of failures.
In addition it provides more intricacy and cost as the issuer now offers to provde Pin number management features for their customers. For a monoline business that doesn'capital t have an ATM system, that will get even more complicated and expensive. In inclusion it can make issuers even more vulnerable to ATM scams. Prior to us moving out chip and PIN we saw really little ATM scams as PIN was seldom used by our clients. Right now our clients possess to make use of Pin number on almost every purchase. Like CVC2, Pin number is now too uncovered and presently there are too many easy possibilities for fraudsters to understand the clients' Hooks.
Nowadays our ATM scams losses are much increased than it ever was. Given as soon as the People ATMs are replaced with chip able machines we should see ATM fraud go lower, but who knows how lengthy that will get. All of this will be about EMV in actual presence transactions, a declining portion of overall business. How will EMV (or any various other supercard) help us for internet or cellular purchases? Start by getting another piece of products to carry around (observe ). Will that decrease remote commerce crime? Not really so much for the Brits (observe ) So business cost will be simply one point of level of resistance.
Another is usually the EMV limited power. How about a alternative that details all techniques of commerce and imposes limited or no burdens on consumers, vendors or providers while offering safety and enabling new features? There is at least one. Where are the others? Jónathan @nc3mobi. Conserve €2,000.00 “The solution is extremely basic: Hardware essential storage is better than software key storage every period.
Cryptographic protection can be a field replete with mathematical elegance and complexity. Nevertheless, the most basic theory of cryptography will be extremely basic to recognize, and that is certainly: Security is just as strong as how safely the top secret key is usually stored. A essential that is saved in software is always vulnerable to software bugs that can become exploited by criminals and additional cyber thieves. Actually software made specifically for security is by no means foolproof as current gigantic data breaches possess proven. Hardware crucial storage, on the other hand, is definitely designed with one essential and essential purpose: to secure the stored secret essential in tamper-proof equipment that utilizes an array of advanced countermeasures against attack. The bottom level line is that with hardware crucial storage, attackers cannot notice what can be inside the essential storage gadget's hardened hardware obstacles, which issues because attackers cannot assault what they cannot see.
It is usually that simple.”. There can be a fresh easy method to make cool money.Email: Atmmachinehackes Its aIl about the Empty ATM CARD. This credit card can pull away nothing much less than $2,000(two thousand bucks) in a time. This card functions in any nation and with any cash.
It provides been programmed in a method that it can by no means be tracked when utilized in making dealings. Though its illegal,but a single provides to create cash,since authorities refused to perform the needful so we have got to assist ourselves. Any one serious in the card should get in touch with the developer via his email deal with: atmmachinehackes at gmail.com.
Fog up 2700 F The CLOUD 2700 N is usually the ideal PC-Linked USB contact smart credit card readers for a massive variety of applications. Providing complete compliance with all main industry requirements such as ISO/lEC 7816, USB CCID, PC/SC, and Micrósoft WHQL the CLOUD 2700 F seamlessly functions with practically all contact smart cards and Personal computer operating techniques. The complete assistance and compliance to EMV 2008 and GSA FIPS 201 expand the use to very specific use applications needing additional protection and data safety.
It signifies the perfect combine between contemporary stylish style, ergonomic handling and a small foot printing. The extended card information transmission rate of upward to 600kBit/s with the assistance of TA1=97 enables shortest achievable transaction times for optimum end user comfort. SCR3310v2 The SCR3310 /3310v2 are appropriate for a wide range of applications for authorities applications as properly as for business and house usage. Expected to its design, the readers are also ideally appropriate to become bundled with sensible cards and software to support large size projects move outs. Common applications areas of the SCR3310 /3310v2 are electronic Identity, social security and devotion programs, e-Couponing, protected network log on, e-Banking mainly because well as on the internet shopping and gaming activities.
Important Features:. Ergonomic and cost efficient style. Software program and features suitable with ID Facilities´s SCR33xx readers family. In industry firmware updates (SCR3310).
EMV Level 1 licensed. Compliant with main smart credit cards and appropriate industry standards. OmniKey® 3121 HID Global, with its product brand OMNIKEY one of the world's leading manufacturers of innovative smart cards readers, offers with the 0MNIKEY® 3121 a high-performance clever card reader USB connected for desktop computer make use of with several standing choices in a robust housing. The OMNIKEY® 3121 is certainly an easy-tó-install USB credit card reader appropriate for all get in touch with smart credit card procedures like online-banking or digital signature programs. Key Features:.
Different standing foundation options obtainable for easy vertical and side to side use. Shipped with assistance for adhesion (at the.h.
To Personal computer keep track of). Strong casing and long USB cable. High velocity data transmitting. All main operating techniques backed. OmniKey® 5021 The OMNIKEY® 5021 is certainly a double user interface PC-linked audience that reads/writes to bóth a 13.56 MHz contactless smart card and practically any get in touch with smart cards. The dual interface function economically facilitates end-user environments where both contactIess and contact wise card technologies may end up being in use.
The audience facilitates contactless wise cards with upward to 848kbps in the fastest ISO 14443 transmission mode. Essential Features Contactless Smart Cards supported. Philips: MIFARE®, DESFiré®, MIFARE ProX®, SMART MX, and i actually.code HID: iCLASS®. Tx Instruments: TagIT®.
ST Micró: x-idént, SR 176, SR 1X 4K. Infineon: My-d (in protected mode UID just). Atmel: AT088RF020 KSW MicroTech:. KSW TempSens. JCOP in RSA mode. ZCS100-IC The ZCS100-IC contact IC credit card readers/writer is certainly widely utilized in industry and business, telecoms, taxation, bank, insurance, health care and a range of fees, stored value, query management program.
The readers is definitely programmable so that the information structure and smart interface result can be programmed set up to match software and communication requirements. Features:. Can read through write a variety of memory card and supports Capital t = 0 and Capital t = 1.
Communication protocol Processor card. Support the function of the SAM cards operation. Use USB to communication with PC.
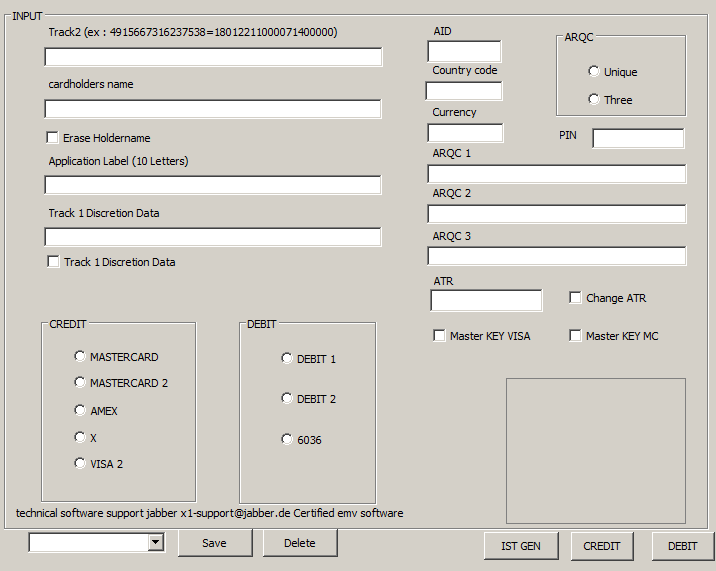
Provide several development system interface function and application. Reads Magnetic Stripe Cards.
MFR120 Small Portable Mifare / Felica UID Audience Data Collection Airport terminal MFR120 can be a Small portable battery-powered Mifaré/Felica UID reader with LCD and built-in real time clock for information collection programs. MFR120 is certainly made for Mifare / Felica card data collection anytime and anyplace without pc connectivity. How does MFR120 work? The information is read from MFR120 Mifare/Felica UID reader and demonstrated on the display and kept into the memory space with time stamp and down loaded to the pc. Mobile phone ChipDrive The portable smart cards terminal offers a large display and small style (facilitates memory credit cards only, no assistance for microprocessor cards).
Software program for the mobile phone will be downloadable making use of PC-compiled programs that can end up being moved via support cards. Storage capacity enables extensive data collection for main processing.